Cryptography and Public Key Infrastructure
1. Cryptography
Cryptography is used to protect information and communications.
This is typically done by using cryptographic techniques to scramble plaintext (ordinary text) into ciphertext (encoded text) and back again.
-
This scrambling process is called encryption.
-
The reverse process is called decryption.
Cryptography is concerned with the following objectives:
-
Confidentiality: The information can be understood by only the intended audience.
-
Integrity: The information cannot be altered in storage or in transit.
-
Non-repudiation: The creator of information cannot later deny that creation.
-
Authentication: The sender and receiver can confirm each other’s identity.
The encryption process requires an algorithm and a key.
-
The algorithm defines how data is transformed from plaintext into ciphertext and back to plaintext.
-
A key is a random string of data used as input to the algorithm.
All of the security of the process is contained in the key. Therefore, the key must be stored securely. The details of the most popular algorithms, however, are publicly available.
There are two types of encryption.
-
Symmetric encryption uses the same key for both encryption and decryption.
-
Asymmetric encryption uses different but mathematically related keys to perform encryption and decryption.
In cryptography, a cryptosystem is a suite of cryptographic algorithms needed to implement a particular security service, most commonly for achieving confidentiality (encryption).
Typically, a cryptosystem consists of three algorithms: one for key generation, one for encryption, and one for decryption.
The term cipher (sometimes cypher) is often used to refer to a pair of algorithms, one for encryption and one for decryption. Therefore, the term cryptosystem is most often used when the key generation algorithm is important. For this reason, the term cryptosystem is commonly used to refer to public key techniques; however both "cipher" and "cryptosystem" are used for symmetric key techniques.
1.1. Symmetric Encryption
Symmetric encryption uses the same key to encrypt plaintext into ciphertext and decrypt ciphertext back into plaintext. The necessary length of the key, expressed in number of bits, is determined by the algorithm. After the key is used to encrypt plaintext, the encrypted message is sent to the recipient who then decrypts the ciphertext.
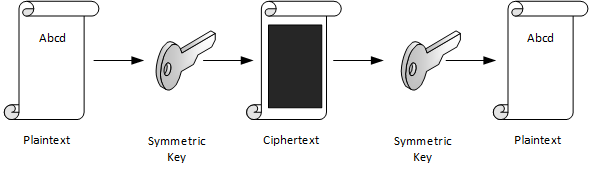
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both encryption of plaintext and decryption of ciphertext.
-
The keys may be identical or there may be a simple transformation to go between the two keys.
-
The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link.
This requirement that both parties have access to the secret key is one of the main drawbacks of symmetric key encryption, in comparison to public-key encryption (also known as asymmetric key encryption).
1.2. Asymmetric Encryption
If only symmetric encryption is used, the problem is that all parties to the communication must possess the private key. However, it is possible that unauthorized third parties can capture the key during transmission to authorized users. To address this issue, use asymmetric or public key cryptography instead.
In asymmetric cryptography, every user has two mathematically related keys called a key pair. One key is public and the other key is private. The key pair ensures that only the recipient has access to the private key needed to decrypt the data. The following illustration summarizes the asymmetric encryption process.
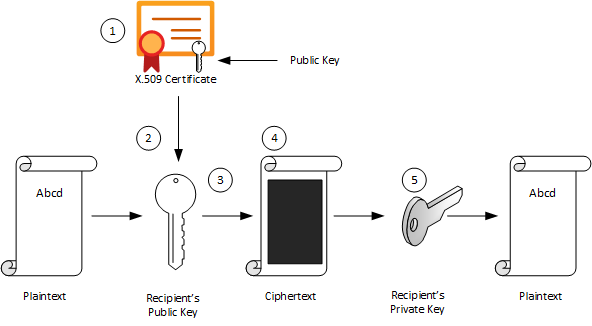
| 1 | The recipient creates a public-private key pair and sends the public key to a CA.
The CA packages the public key in an X.509 certificate. |
| 2 | The sending party obtains the recipient’s public key from the CA. |
| 3 | The sender encrypts plaintext data using an encryption algorithm.
The recipient’s public key is used to perform encryption. |
| 4 | The sender transmits the ciphertext to the recipient.
It isn’t necessary to send the key because the recipient already has the private key needed to decrypt the ciphertext. |
| 5 | The recipient decrypts the ciphertext by using the specified asymmetric algorithm and the private key. |
Public-key cryptography, or asymmetric cryptography, is a cryptographic system that uses public-private key pair of keys:
-
public keys which may be disseminated widely,
-
and private keys which are known only to the owner.
The generation of such keys depends on cryptographic algorithms based on mathematical problems to produce one-way functions. Effective security only requires keeping the private key private; the public key can be openly distributed without compromising security.
In such a system, any person can encrypt a message using the receiver’s public key, but that encrypted message can only be decrypted with the receiver’s private key.
1.2.1. Asymmetric Signing
Asymmetric algorithms can be used to protect data from modification (integrity) and prove the identity of the data creator (non-repudiation). The following illustration shows how asymmetric signing helps prove the sender’s identity.
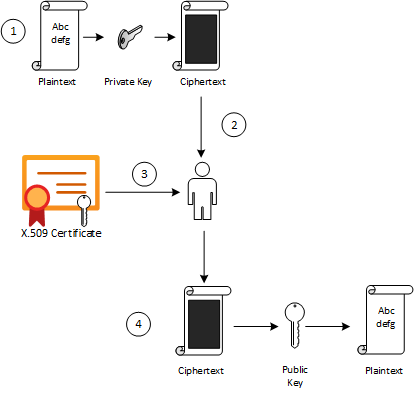
| 1 | The sender passes plaintext data through an asymmetric encryption algorithm, using the private key for encryption.
Notice that this scenario reverses use of the private and public keys outlined in the preceding section that detailed asymmetric encryption. |
| 2 | The resulting ciphertext is sent to the recipient. |
| 3 | The recipient obtains the originator’s public key from a directory. |
| 4 | The recipient decrypts the ciphertext by using the originator’s public key.
The resulting plaintext proves the originator’s identity because only the originator has access to the private key that initially encrypted the original text. |
1.2.2. RSA (Rivest-Shamir-Adleman)
RSA (Rivest—Shamir—Adleman) is one of the first public-key cryptosystems and is widely used for secure data transmission.
In such a cryptosystem, the encryption key is public and it is different from the decryption key which is kept secret (private).
The acronym RSA is made of the initial letters of the surnames of Ron Rivest, Adi Shamir, and Leonard Adleman, who first publicly described the algorithm in 1978.
RSA is a relatively slow algorithm, and because of this, it is less commonly used to directly encrypt user data.
More often, RSA passes encrypted shared keys for symmetric key cryptography which in turn can perform bulk encryption-decryption operations at much higher speed.
1.3. Combining Symmetric and Asymmetric Encryption
Symmetric and asymmetric encryption can be combined to take advantage of their relative strengths.
Symmetric encryption is much faster than asymmetric but, because of the necessity of sending private keys to other parties, is not as secure.
To combine the two types together,
-
symmetric encryption can be used to convert plaintext to ciphertext.
-
Asymmetric encryption is used to exchange the symmetric key.
This is demonstrated by the following diagram.
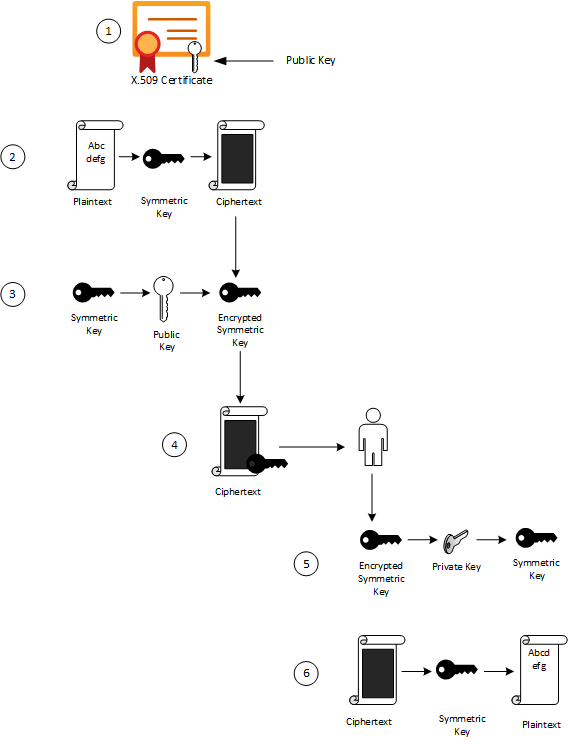
| 1 | The sender retrieves the recipient’s public key. |
| 2 | The sender generates a symmetric key and uses it to encrypt the original data. |
| 3 | The sender uses the recipient’s public key to encrypt the symmetric key. |
| 4 | The sender transmits the encrypted symmetric key and the ciphertext to the intended recipient. |
| 5 | The recipient uses the private key that matches the recipient’s public key to decrypt the sender’s symmetric key. |
| 6 | The recipient uses the symmetric key to decrypt the ciphertext. |
1.4. Signing
Digital signing can be used to determine whether the data has been modified in transit or at rest.
-
The data is passed through a hash algorithm, a one-way function that produces a mathematical result from the given message.
-
The result is called a hash value, message digest, digest, signature, or thumbprint.
-
A hash value cannot be reversed to obtain the original message.
Because a small change in the message results in a significant change in the thumbprint, the hash value can be used to determine whether a message has been altered.
The following illustration shows how asymmetric encryption and hash algorithms can be used to verify that a message has not been modified.
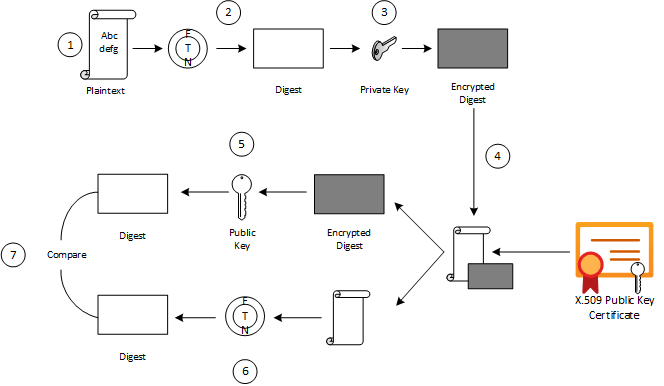
| 1 | The sender creates a plaintext message. |
| 2 | The sender hashes the plaintext message to create a message digest. |
| 3 | The sender encrypts the digest using a private key. |
| 4 | The sender transmits the plaintext message and the encrypted digest to the intended recipient. |
| 5 | The recipient decrypts the digest by using the sender’s public key. |
| 6 | The recipient runs the same hash algorithm that the sender used over the message. |
| 7 | The recipient compares the resulting signature to the decrypted signature.
If the digests are the same, the message was not modified during transmission. |
2. ASN.1, DER and PEM
2.1. Abstract Syntax Notation One (ASN.1)
Abstract Syntax Notation One (ASN.1) is a standard interface description language for defining data structures that can be serialized and deserialized in a cross-platform way.
It is broadly used in telecommunications and computer networking, and especially in cryptography.
The advantage is that the ASN.1 description of the data encoding is independent of a particular computer or programming language.
Because ASN.1 is both human-readable and machine-readable, an ASN.1 compiler can compile modules into libraries of code, codecs, that decode or encode the data structures.
2.2. X.690 BER CER DER
X.690 is an ITU-T standard specifying several ASN.1 encoding formats:
-
Basic Encoding Rules (BER)
-
Canonical Encoding Rules (CER)
-
Distinguished Encoding Rules (DER)
The Basic Encoding Rules were the original rules laid out by the ASN.1 standard for encoding abstract information into a concrete data stream.
The rules, collectively referred to as a transfer syntax in ASN.1 parlance, specify the exact octet sequences which are used to encode a given data item.
The syntax defines such elements as:
-
the representations for basic data types,
-
the structure of length information,
-
and the means for defining complex or compound types based on more primitive types.
The BER syntax, along with two subsets of BER (the CER and the DER), are defined by the ITU-T’s X.690 standards document, which is part of the ASN.1 document series.
2.3. Privacy-Enhanced Mail (PEM)
Privacy-Enhanced Mail (PEM) is a de facto file format for storing and sending cryptographic keys, certificates, and other data, based on a set of 1993 IETF standards defining "privacy-enhanced mail."
Many cryptography standards use ASN.1 to define their data structures, and Distinguished Encoding Rules (DER) to serialize those structures.
Because DER produces binary output, it can be challenging to transmit the resulting files through systems, like electronic mail, that only support ASCII.
The PEM format solves this problem by encoding the binary data using base64.
-
PEM also defines a one-line header, consisting of -----BEGIN, a label, and -----, and a one-line footer, consisting of -----END, a label, and -----.
-
The label determines the type of message encoded.
-
Common labels include CERTIFICATE, CERTIFICATE REQUEST, PRIVATE KEY and X509 CRL.
PEM data is commonly stored in files with a
-
".pem" suffix, a ".cer"
-
or ".crt" suffix (for certificates),
-
or a ".key" suffix (for public or private keys).
The label inside a PEM file represents the type of the data more accurately than the file suffix, since many different types of data can be saved in a ".pem" file.
In particular PEM refers to the header and base64 wrapper for a binary format contained within, but does not specify any type or format for the binary data, so that a PEM file may contain "almost anything base64 encoded and wrapped with BEGIN and END lines".
A PEM file may contain multiple instances.
-
For instance, an operating system might provide a file containing a list of trusted CA certificates,
-
or a web server might be configured with a "chain" file containing an end-entity certificate plus a list of intermediate certificates.
3. Public Key Cryptography Standards (PKCS)
In cryptography, PKCS stands for "Public Key Cryptography Standards".
These are a group of public-key cryptography standards devised and published by RSA Security LLC, starting in the early 1990s.
The company published the standards to promote the use of the cryptography techniques to which they had patents, such as the RSA algorithm, the Schnorr signature algorithm and several others.
Though not industry standards (because the company retained control over them), some of the standards in recent years have begun to move into the "standards-track" processes of relevant standards organizations such as the IETF and the PKIX working-group.
| Version | Name | Comments | |
|---|---|---|---|
PKCS #1 |
2.2 |
RSA Cryptography Standard |
See RFC 8017. Defines the mathematical properties and format of RSA public and private keys (ASN.1-encoded in clear-text), and the basic algorithms and encoding/padding schemes for performing RSA encryption, decryption, and producing and verifying signatures. |
PKCS #7 |
1.5 |
Cryptographic Message Syntax Standard |
See RFC 2315. Used to sign and/or encrypt messages under a PKI. Used also for certificate dissemination (for instance as a response to a PKCS #10 message). Formed the basis for S/MIME, which is as of 2010 based on RFC 5652, an updated Cryptographic Message Syntax Standard (CMS). Often used for single sign-on. |
PKCS #8 |
1.2 |
Private-Key Information Syntax Standard |
See RFC 5958. Used to carry private certificate keypairs (encrypted or unencrypted). |
PKCS #10 |
1.7 |
Certification Request Standard |
See RFC 2986. Format of messages sent to a certification authority to request certification of a public key. See certificate signing request. |
PKCS #12 |
1.1 |
Personal Information Exchange Syntax Standard |
See RFC 7292. Defines a file format commonly used to store private keys with accompanying public key certificates, protected with a password-based symmetric key. PFX is a predecessor to PKCS #12. + This container format can contain multiple embedded objects, such as multiple certificates. Usually protected/encrypted with a password. |
3.1. PKCS #1
In cryptography, PKCS #1 is the first of a family of standards called Public-Key Cryptography Standards (PKCS), published by RSA Laboratories.
-
It provides the basic definitions of and recommendations for implementing the RSA algorithm for public-key cryptography.
-
It defines
-
the mathematical properties of public and private keys,
-
primitive operations for encryption and signatures,
-
secure cryptographic schemes,
-
and related ASN.1 syntax representations.
-
$ openssl genrsa -out pkc1.pem 512
Generating RSA private key, 512 bit long modulus (2 primes)
.....+++++++++++++++++++++++++++
.........+++++++++++++++++++++++++++
e is 65537 (0x010001)
$ cat pkc1.pem
-----BEGIN RSA PRIVATE KEY-----
MIIBOwIBAAJBAPpyrGCXa2k1hGUuGSDTVxGKoWzBO+YHKZ7xdkxnvqWJyHnvxXQS
06DmVFRt20LYtgAx3TN/C4dz98C/FW/Ryc0CAwEAAQJBAJa0Il4NP6kTdxObZauH
AMGhdfmHXY/Rh44JJnJbizD4Q1pTglSMLPDWMMZP2ojlNlTJINN+BsuotCnyeUXj
QFECIQD9qfYNkn5e5PRfSsySjT/wKgyEwvDGXpFU8LXJWC454wIhAPzBIVacmP2L
B9YOiJWxrXJk9otG/c5GnqhndCB+LPyPAiA773W43T1ItLZc8bKGiiNqXrUYhWsY
o+2Y8UsyqMg7WwIhAK5dIX2ZnGVUszw1XH5AS5JeGkLs34yc5Tjx3YfI44n7AiBL
Q60mfKn/P4J4aVzYqTkFLPpprieOTbveV4vUlqf7/Q==
-----END RSA PRIVATE KEY-----
$ openssl pkcs8 -in rsa.pem -topk8 -nocrypt
-----BEGIN PRIVATE KEY-----
MIIBVQIBADANBgkqhkiG9w0BAQEFAASCAT8wggE7AgEAAkEAtiT1WDsvrECjWC2n
At+yPN/fWl7jWHHOEd0XH3ra5A9QEw9tR59AJiqE+HlveygetOHp399VHOFmsdQp
4AeYnwIDAQABAkEAi2bx11tE+0JlQaF/BvYJxglZOiMRQKmpG4booZE3Yf8DGG78
rxwTGvyPFQhv+rrDeeqtW+snMZbBNXZvjYtGYQIhAOViHfmDXQ5qEVlc3NLgWBG1
+l7oh7ZiMZHUr5faOtl5AiEAy0eZTXoV0fM4yygvX54i+jhfjxjnGCq/aiamj5Kp
lNcCIQCVyr4CS4uANzm/HopB1ykL38dxJO5C5tqx/a7xPhyCGQIgJ5J6n4CCuupU
Rgg+oKiSOo+62oqIgkXgGXQIvK5aYOUCIEAoNlXayIK3vB4GNDtnNkOp+sW23fw8
X4CTyXy2l/Qi
-----END PRIVATE KEY-----3.2. PKCS #7
In cryptography, "PKCS #7: Cryptographic Message Syntax" (a.k.a. "CMS") is a standard syntax for storing signed and/or encrypted data.
-
PKCS #7 files may be stored both as raw DER format or as PEM format.
-
PEM format is the same as DER format but wrapped inside Base64 encoding and sandwiched in between ----BEGIN PKCS7---- and ----END PKCS7----.
-
Windows uses the ".p7b" file name extension for both these encodings.
A typical use of a PKCS #7 file would be to store certificates and/or certificate revocation lists.
Here’s an example of how to first download a certificate, then wrap it inside a PKCS #7 archive and then read from that archive:
$ openssl s_client -connect local.io:443 -xcertform PEM </dev/null 2>/dev/null | openssl x509 > local.io.pem
$ openssl crl2pkcs7 -nocrl -certfile local.io.pem -out local.io.p7b
$ openssl pkcs7 -in local.io.p7b -noout -print_certs
subject=C = CN, ST = Shanghai, L = Shanghai, O = Global Security, OU = IT Department, CN = *.local.io
issuer=C = CN, ST = Shanghai, L = Shanghai, O = Global Security, OU = IT Department, CN = *.local.io3.3. PKCS #8
In cryptography, PKCS #8 is a standard syntax for storing private key information.
The PKCS #8 private key may be encrypted with a passphrase using the PKCS #5 standards, which supports multiple ciphers.
PKCS #8 private keys are typically exchanged in the PEM base64-encoded format, for example:
$ openssl genpkey -algorithm RSA \
-pkeyopt rsa_keygen_bits:512 -out key.pem # 512 bits is a weak key, please specify 2048+ bits.
.................+++++++++++++++++++++++++++
........+++++++++++++++++++++++++++
$ cat key.pem
-----BEGIN PRIVATE KEY-----
MIIBVAIBADANBgkqhkiG9w0BAQEFAASCAT4wggE6AgEAAkEAuGVDfMa5TyUZIEW0
pgvlN/xajzoaDe9yV6GDqqUHdBU/NtaynIXSkxEoupkGUBGama0OXI8TzpUJCjcR
IkkAbwIDAQABAkBhPy6HaLqkLdmBdqGeDJn3m8Qa0zaYcNaptomc/mne4svm2K1x
GVaNAFBlS3eFd8u/gYJHpCKBlVcBmWkabZhxAiEA6fOr7roNKOM9OyM3//sWhT0Z
B0uthEo4GLqRCgdt9/kCIQDJxf7v7UtUIPeYm+fSYaL4kb35RBpr1zsm77w6YC9l
pwIhAN8/ARA7RheAUIvAHc4Ngf3+wYVut9OHJ2Shk4nocQ2xAiAfY1ikVEK6pKI/
sEkg1iV3C50E8M43ZnUCOpsKbboR0wIgYIjtYrXncmuxnSnUXrr3A0yEU5feX1h6
n+hSMkACSC4=
-----END PRIVATE KEY-----
$ openssl pkey -in key.pem -pubout
-----BEGIN PUBLIC KEY-----
MFwwDQYJKoZIhvcNAQEBBQADSwAwSAJBALhlQ3zGuU8lGSBFtKYL5Tf8Wo86Gg3v
clehg6qlB3QVPzbWspyF0pMRKLqZBlARmpmtDlyPE86VCQo3ESJJAG8CAwEAAQ==
-----END PUBLIC KEY-----
$ openssl pkcs8 -in key.pem -topk8
Enter Encryption Password:
Verifying - Enter Encryption Password:
-----BEGIN ENCRYPTED PRIVATE KEY-----
MIIBvTBXBgkqhkiG9w0BBQ0wSjApBgkqhkiG9w0BBQwwHAQIrXICjrjhXx8CAggA
MAwGCCqGSIb3DQIJBQAwHQYJYIZIAWUDBAEqBBCGwam45e0nuiAGJLqz/7UcBIIB
YCgOeAEb8rCnnVSeiL5jzD0KxUAA9PQ8FHTFjrrSeFHkUF3FTdJDxFgCeXyhErtJ
ty4X9jf28+l9x9FYZoqrB9LiIX+ntMhtmEiAj5n0vML1FCheGdXstJC2v3l4f0x3
u/Fv5DJaVnYKKECo62xDDE41eZHTJLZDUdJTo7r210M6hopxL4fnwvekEQF7Awi3
eQBR6uif5uTUlidw0czvEt5YLeOURzXW9y9AvM7onx32sU/mmqc8Gp2i/0hOs0SG
0XC5LYmnZ/5WJSn0lwtoNl1ZAmOA73/D8cO6mHp1+pBT2jM3tWpXy7Cywb4OAHQy
8Gg6A5HmULKf5hzQBGjWiD2ZD2fEHQP8rmilE0s+JvifWmmFfLiTuO4xCgH82XE9
77Hj7yk1Rp4ewQpfau58yKxjjETHRTOosM/rWaC9oDCzSuOuuPApiQyHdYD9/Ylg
m1SedRD9NuA2pE3oK3X42yM=
-----END ENCRYPTED PRIVATE KEY-----3.4. PKCS #10
In public key infrastructure (PKI) systems, a certificate signing request (also CSR or certification request) is a message sent from an applicant to a {certificate_authority}[certificate authority] in order to apply for a digital identity certificate.
It usually contains the public key for which the certificate should be issued, identifying information (such as a domain name) and integrity protection (e.g., a digital signature).
The most common format for CSRs is the PKCS #10 specification and another is the Signed Public Key and Challenge SPKAC format generated by some web browsers.
Before creating a CSR, the applicant first generates a key pair, keeping the private key secret.
The CSR contains information identifying the applicant (such as a distinguished name in the case of an X.509 certificate) which must be signed using the applicant’s private key.
The CSR also contains the public key chosen by the applicant.
The CSR may be accompanied by other credentials or proofs of identity required by the certificate authority, and the certificate authority may contact the applicant for further information.
A certification request consists of three main parts:
-
the certification request information,
-
a signature algorithm identifier,
-
and a digital signature on the certification request information.
The first part contains the significant information, including the public key.
The signature by the requester prevents an entity from requesting a bogus certificate of someone else’s public key. Thus the private key is needed to produce, but it is not part of, the CSR.
The PKCS#10 standard defines a binary format (DER) for encoding CSRs expressed in ASN.1.
A CSR may also be represented as a Base64 encoded PKCS#10 (PEM).
$ openssl genrsa -out key.pem 2048
Generating RSA private key, 2048 bit long modulus (2 primes)
.............................+++++
....+++++
e is 65537 (0x010001)
$ openssl req -x509 -new -key key.pem -subj "/CN=example.com" -out req.pem
$ cat req.pem
-----BEGIN CERTIFICATE-----
MIIDDTCCAfWgAwIBAgIUQ7SPGfNcoaVJ5m/I6Hyley7IG2gwDQYJKoZIhvcNAQEL
BQAwFjEUMBIGA1UEAwwLZXhhbXBsZS5jb20wHhcNMjExMjIxMDcyMTIyWhcNMjIw
MTIwMDcyMTIyWjAWMRQwEgYDVQQDDAtleGFtcGxlLmNvbTCCASIwDQYJKoZIhvcN
AQEBBQADggEPADCCAQoCggEBALSzGjH++EooGvOGZgkfOBWGHMc8GXnMS1Pst+S8
O/IgF1rsDffGOFLtKCsMoSIwc6qq3Et8N9mnwORITjp1fVdhAToeWAsGim4evRRf
1YUSghtbO/BGeu19sbgnGHqA3ExO5lm2zcE3TxgIZkOkYQAgLbR/svav922xj85Z
HsuvnOPxemWNUxCCBsucu95QhQ5CLTjNDkxfPV9B9V6OfdhpoOtQowKt5ueUvLqt
1L+EgetUxnHz9+rPBBgO22qgvcVnkIn0oAJ8/s8s1BUhtNdvILZ1cAwEOGqNbya2
IL0Z5U+UUhiprC4o80K9EBDvU/xQUX524EjlD0wZq7Ncn2MCAwEAAaNTMFEwHQYD
VR0OBBYEFL6KbULLcDDedyr4opkFYg6owGOBMB8GA1UdIwQYMBaAFL6KbULLcDDe
dyr4opkFYg6owGOBMA8GA1UdEwEB/wQFMAMBAf8wDQYJKoZIhvcNAQELBQADggEB
AKnFgZPtyU9UXNxoO4C2vOxTix9oVwx02q2oQJpwZdviO83r8Z8FE6/ZX+GdVEAz
g9btu/relajtaZwUzz9PSAA7W6j123tzu8USU7iROaRFFV6zejk/qxk0ahibNato
WQCxemcIev1FiA9bR9m3q84K7etEb9+mO+MYXPzvOZsRE/g52h9X34+ZuRlxCutC
oI6Nv4Bj61t5a/7jcBBDJCXQ4iI6GhVyYw/o2NeYpjmLVrxbDu4+oQ9l/JQYMBz9
9JcZOp5K5HL4fLj6UJYP/o0tJSBar2Db08Z16btSFnBXlnR02elfeLYx9mz6fdlt
/268X2cHeQJtLTfNvk5LFuU=
-----END CERTIFICATE-----
$ openssl asn1parse -i -in req.pem
0:d=0 hl=4 l= 781 cons: SEQUENCE
4:d=1 hl=4 l= 501 cons: SEQUENCE
8:d=2 hl=2 l= 3 cons: cont [ 0 ]
10:d=3 hl=2 l= 1 prim: INTEGER :02
13:d=2 hl=2 l= 20 prim: INTEGER :43B48F19F35CA1A549E66FC8E87CA57B2EC81B68
35:d=2 hl=2 l= 13 cons: SEQUENCE
37:d=3 hl=2 l= 9 prim: OBJECT :sha256WithRSAEncryption
48:d=3 hl=2 l= 0 prim: NULL
50:d=2 hl=2 l= 22 cons: SEQUENCE
52:d=3 hl=2 l= 20 cons: SET
54:d=4 hl=2 l= 18 cons: SEQUENCE
56:d=5 hl=2 l= 3 prim: OBJECT :commonName
61:d=5 hl=2 l= 11 prim: UTF8STRING :example.com
...4. Public Key Certificates
In cryptography, a public key certificate, also known as a digital certificate or identity certificate, is an electronic document used to prove the ownership of a public key.
The certificate includes information about the key, information about the identity of its owner (called the subject), and the digital signature of an entity that has verified the certificate’s contents (called the issuer).
If the signature is valid, and the software examining the certificate trusts the issuer, then it can use that key to communicate securely with the certificate’s subject.
In email encryption, code signing, and e-signature systems, a certificate’s subject is typically a person or organization.
However, in Transport Layer Security (TLS) a certificate’s subject is typically a computer or other device, though TLS certificates may identify organizations or individuals in addition to their core role in identifying devices.
TLS, sometimes called by its older name Secure Sockets Layer (SSL), is notable for being a part of HTTPS, a protocol for securely browsing the web.
In a typical public-key infrastructure (PKI) scheme, the certificate issuer is a certificate authority (CA), usually a company that charges customers to issue certificates for them. By contrast, in a web of trust scheme, individuals sign each other’s keys directly, in a format that performs a similar function to a public key certificate.
The most common format for public key certificates is defined by X.509.
Because X.509 is very general, the format is further constrained by profiles defined for certain use cases, such as Public Key Infrastructure (X.509) as defined in RFC 5280.
5. X.509 Public Key Certificates
In cryptography, X.509 is a standard defining the format of public key certificates.
X.509 certificates are used in many Internet protocols, including TLS/SSL, which is the basis for HTTPS, the secure protocol for browsing the web.
They are also used in offline applications, like electronic signatures.
X.509 certificates are digital documents that represent a user, computer, service, or device.
-
They are issued by a certification authority (CA), subordinate CA, or registration authority or self-signed and contain the public key of the certificate subject.
-
They do not contain the subject’s private key which must be stored securely.
Public key certificates are documented by RFC 5280. They are digitally signed and, in general, contain the following information:
-
Information about the certificate subject
-
The public key that corresponds to the subject’s private key
-
Information about the issuing CA
-
The supported encryption and/or digital signing algorithms
-
Information to determine the revocation and validity status of the certificate
When a certificate is signed by a trusted certificate authority, or validated by other means, someone holding that certificate can rely on the public key it contains to establish secure communications with another party, or validate documents digitally signed by the corresponding private key.
5.1. Certificate Fields
Over time there have been three certificate versions. Each version adds fields to the one before. Version 3 is current and contains version 1 and version 2 fields in addition to version 3 fields.
Version 1 defined the following fields:
-
Version: A value (1, 2, or 3) that identifies the version number of the certificate
-
Serial Number: A unique number for each certificate issued by a CA
-
CA Signature Algorithm: Name of the algorithm the CA uses to sign the certificate contents
-
Issuer Name: The distinguished name (DN) of the certificate’s issuing CA
-
Validity Period: The time period for which the certificate is considered valid
-
Subject Name: Name of the entity represented by the certificate
-
Subject Public Key Info: Public key owned by the certificate subject
Version 2 added the following fields containing information about the certificate issuer. These fields are, however, rarely used.
-
Issuer Unique ID: A unique identifier for the issuing CA as defined by the CA
-
Subject Unique ID: A unique identifier for the certificate subject as defined by the issuing CA
Version 3 certificates added the following extensions:
-
Authority Key Identifier: This can be one of two values:
-
The subject of the CA and serial number of the CA certificate that issued this certificate
-
A hash of the public key of the CA that issued this certificate
-
-
Subject Key Identifier: Hash of the current certificate’s public key
-
Key Usage Defines the service for which a certificate can be used.
This can be one or more of the following values:
-
Digital Signature
-
Non-Repudiation
-
Key Encipherment
-
Data Encipherment
-
Key Agreement
-
Key Cert Sign
-
CRL Sign
-
Encipher Only
-
Decipher Only
-
-
Private Key Usage Period: Validity period for the private key portion of a key pair
-
Certificate Policies: Policies used to validate the certificate subject
-
Policy Mappings: Maps a policy in one organization to policy in another
-
Subject Alternative Name: List of alternate names for the subject
-
Issuer Alternative Name: List of alternate names for the issuing CA
-
Subject Dir Attribute: Attributes from an X.500 or LDAP directory
-
Basic Constraints: Allows the certificate to designate whether it is issued to a CA, or to a user, computer, device, or service.
This extension also includes a path length constraint that limits the number of subordinate CAs that can exist.
-
Name Constraints: Designates which namespaces are allowed in a CA-issued certificate
-
Policy Constraints: Can be used to prohibit policy mappings between CAs
-
Extended Key Usage: Indicates how a certificate’s public key can be used beyond the purposes identified in the Key Usage extension
-
CRL Distribution Points: Contains one or more URLs where the base certificate revocation list (CRL) is published
-
Inhibit anyPolicy: Inhibits the use of the All Issuance Policies OID (2.5.29.32.0) in subordinate CA certificates
-
Freshest CRL: Contains one or more URLs where the issuing CA’s delta CRL is published
-
Authority Information Access: Contains one or more URLs where the issuing CA certificate is published
-
Subject Information Access: Contains information about how to retrieve additional details for a certificate subject
5.2. Certificate Formats
There are several commonly used filename extensions for X.509 certificates.
-
.pem – (Privacy-enhanced Electronic Mail) Base64 encoded DER certificate, enclosed between "-----BEGIN CERTIFICATE-----" and "-----END CERTIFICATE-----"
-
.cer, .crt, .der – usually in binary DER form, but Base64-encoded certificates are common too
-
.p7b, .p7c – PKCS#7 SignedData structure without data, just certificate(s) or CRL(s)
-
.p12 – PKCS#12, may contain certificate(s) (public) and private keys (password protected)
-
.pfx – PFX, predecessor of PKCS#12 (usually contains data in PKCS#12 format, e.g., with PFX files generated in IIS)
PKCS#7 is a standard for signing or encrypting (officially called "enveloping") data. Since the certificate is needed to verify signed data, it is possible to include them in the SignedData structure. A .P7C file is a degenerated SignedData structure, without any data to sign.
PKCS#12 evolved from the personal information exchange (PFX) standard and is used to exchange public and private objects in a single file.
6. OpenSSL
OpenSSL is a software library for applications that secure communications over computer networks against eavesdropping or need to identify the party at the other end. It is widely used in Internet web servers, serving a majority of all web sites.
OpenSSL contains an open-source implementation of the SSL and TLS protocols. The core library, written in the C programming language, implements basic cryptographic functions and provides various utility functions. Wrappers allowing the use of the OpenSSL library in a variety of computer languages are available.
The OpenSSL Software Foundation (OSF) represents the OpenSSL project in most legal capacities including contributor license agreements, managing donations, and so on. OpenSSL Software Services (OSS) also represents the OpenSSL project, for Support Contracts.
Versions are available for most Unix and Unix-like operating systems (including Solaris, Linux, macOS, QNX, and the various open-source BSD operating systems), OpenVMS and Microsoft Windows.
OPENSSL(1SSL) OpenSSL OPENSSL(1SSL)
NAME
openssl - OpenSSL command line tool
SYNOPSIS
openssl command [ command_opts ] [ command_args ]
openssl list [ standard-commands | digest-commands | cipher-commands | cipher-algorithms | digest-algorithms | public-key-algorithms]
openssl no-XXX [ arbitrary options ]
DESCRIPTION
OpenSSL is a cryptography toolkit implementing the Secure Sockets Layer (SSL v2/v3) and Transport Layer Security (TLS v1) network protocols and related
cryptography standards required by them.
The openssl program is a command line tool for using the various cryptography functions of OpenSSL's crypto library from the shell. It can be used for
o Creation and management of private keys, public keys and parameters
o Public key cryptographic operations
o Creation of X.509 certificates, CSRs and CRLs
o Calculation of Message Digests
o Encryption and Decryption with Ciphers
o SSL/TLS Client and Server Tests
o Handling of S/MIME signed or encrypted mail
o Time Stamp requests, generation and verification
COMMAND SUMMARY
The openssl program provides a rich variety of commands (command in the SYNOPSIS above), each of which often has a wealth of options and arguments
(command_opts and command_args in the SYNOPSIS).
Detailed documentation and use cases for most standard subcommands are available (e.g., x509(1) or openssl-x509(1)).
Standard Commands
asn1parse
Parse an ASN.1 sequence.
genpkey
Generation of Private Key or Parameters.
pkcs12
PKCS#12 Data Management.
pkcs7
PKCS#7 Data Management.
pkcs8
PKCS#8 format private key conversion tool.
pkey
Public and private key management.
pkeyutl
Public key algorithm cryptographic operation utility.
req
PKCS#10 X.509 Certificate Signing Request (CSR) Management.
s_client
This implements a generic SSL/TLS client which can establish a transparent connection to a remote server speaking SSL/TLS. It's intended for testing
purposes only and provides only rudimentary interface functionality but internally uses mostly all functionality of the OpenSSL ssl library.
x509
X.509 Certificate Data Management.6.1. Self-signed Certificate
-
Generate a self signed root certificate
openssl req -x509 \ -nodes \ -newkey rsa:2048 -keyout key.pem \ -days 30 \ -out cert.pem \ -subj "/C=CN/ST=Shanghai/L=Shanghai/O=Global Security/OU=IT Department/CN=example.com" \ -addext "subjectAltName=DNS:example.com,DNS:*.example.com" -
Generate a self signed root certificate from a private key
# Generate a 2048 bit RSA key (same as: openssl genrsa -out key.pem 2048) openssl genpkey \ -algorithm RSA \ -pkeyopt rsa_keygen_bits:2048 \ -out key.pem # Generate a certificate request from a private key openssl req -x509 \ -new \ -key key.pem \ -subj "/C=CN/ST=Shanghai/L=Shanghai/O=Global Security/OU=IT Department/CN=example.com" \ -addext "subjectAltName=DNS:example.com,DNS:*.example.com" \ -out cert.pem # Display the subject and fingerprint of the cert cert.pem openssl x509 -in cert.pem -subject -ext subjectAltName -fingerprint -noout 2>/dev/nullsubject=C = CN, ST = Shanghai, L = Shanghai, O = Global Security, OU = IT Department, CN = example.com X509v3 Subject Alternative Name: DNS:example.com, DNS:*.example.com SHA1 Fingerprint=43:FA:67:3F:45:95:93:5D:25:BE:15:2E:F1:C4:98:1D:8F:52:77:07# Calculate the fingerprint/thumbprint with .der format $ openssl x509 -in baidu.pem -outform der | sha1sum 43fa673f4595935d25be152ef1c4981d8f527707 -
6.2. Show Certificate:
$ openssl x509 -in cert.pem -noout -issuer
issuer=C = CN, ST = Shanghai, L = Shanghai, O = Global Security, OU = IT Department, CN = example.com
$ openssl x509 -in cert.pem -noout -subject
subject=C = CN, ST = Shanghai, L = Shanghai, O = Global Security, OU = IT Department, CN = example.com
$ openssl x509 -in cert.pem -noout -fingerprint
SHA1 Fingerprint=1A:EB:13:40:38:AD:2E:42:57:A6:8A:BB:09:7A:5B:70:8B:69:C6:20
$ openssl x509 -in cert.pem -noout -dates
notBefore=Nov 9 06:46:15 2021 GMT
notAfter=Dec 9 06:46:15 2021 GMT
$ openssl x509 -in cert.pem -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
6d:5e:9d:a3:cc:6f:b8:51:13:46:f6:70:74:cd:3b:6f:ef:5c:6d:6f
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = CN, ST = Shanghai, L = Shanghai, O = Global Security, OU = IT Department, CN = example.com
Validity
Not Before: Dec 21 07:49:22 2021 GMT
Not After : Jan 20 07:49:22 2022 GMT
Subject: C = CN, ST = Shanghai, L = Shanghai, O = Global Security, OU = IT Department, CN = example.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:e3:af:8b:6a:2d:63:57:d8:66:01:68:1d:00:39:
15:82:e9:d2:9b:8c:77:2b:94:99:6f:b3:b4:43:d5:
0e:64:07:32:82:2b:09:96:ce:1f:16:3b:39:dc:13:
77:76:a9:3f:52:09:6f:5c:c8:35:cc:06:b0:a0:39:
38:ed:37:19:32:fb:6c:37:6f:d8:e5:1c:d0:52:eb:
be:c5:de:df:90:8d:3e:cc:0a:1a:d8:ce:27:06:54:
5e:b5:d6:68:89:2d:80:d3:09:ef:92:5a:ed:7a:d4:
e6:7f:dc:6c:9b:cc:a3:63:fc:9a:cf:98:30:b1:26:
a2:25:a4:ea:87:d0:de:d8:b3:83:0b:09:35:34:4b:
84:20:dd:dd:4c:67:88:a6:bf:84:b6:2d:0f:62:e1:
19:08:f0:f7:05:45:3f:9a:cf:28:33:58:e1:ad:43:
bc:b0:51:36:e0:5e:22:f6:95:2f:6a:e3:67:a4:9a:
c2:91:fa:d4:94:27:09:4f:56:d1:57:76:c3:0d:d0:
74:10:f4:02:44:21:4e:b6:29:50:02:8a:01:3e:60:
41:83:af:d2:13:96:05:ad:9f:07:41:2f:ca:f5:67:
d5:75:97:48:5a:8f:70:a4:34:df:24:e6:d0:30:6a:
c3:a4:7c:7f:5f:34:ac:12:aa:f8:60:72:77:00:93:
63:bd
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
DB:44:E6:DA:66:DB:31:57:9D:CF:33:FF:36:3A:D3:B8:4F:6D:E0:86
X509v3 Authority Key Identifier:
keyid:DB:44:E6:DA:66:DB:31:57:9D:CF:33:FF:36:3A:D3:B8:4F:6D:E0:86
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Subject Alternative Name:
DNS:example.com, DNS:*.example.com
Signature Algorithm: sha256WithRSAEncryption
d5:89:de:d1:1d:7a:f2:87:76:32:9c:5a:79:8a:af:0f:6a:44:
e5:cb:d5:85:14:5f:a5:f6:08:6c:30:82:ad:99:c2:1f:ca:a2:
56:51:fa:f6:db:64:cd:cf:f4:72:c7:50:84:2d:6f:c6:bf:fa:
fd:ca:36:80:2a:d1:35:71:87:7f:c2:49:aa:bf:23:da:0b:76:
3b:75:d7:20:c1:60:5a:4b:74:35:ac:3a:cc:a3:bc:b8:dd:a9:
76:93:11:ef:e3:fd:f6:c6:dd:eb:46:f1:e3:98:41:6e:aa:b5:
69:ee:22:d1:5d:55:8e:db:1f:5b:87:a9:9a:0b:45:20:55:36:
e1:34:2e:0e:a0:53:79:51:30:e4:48:65:ae:ec:d5:9e:be:48:
65:2d:ca:86:5d:01:5f:df:46:62:bc:ab:3c:03:67:96:95:81:
43:1d:05:66:3d:6b:11:30:9e:7f:61:11:89:b8:3c:41:a5:05:
9f:81:d3:14:5b:6d:63:f7:af:ca:71:3c:51:96:ab:72:9a:29:
d1:68:e3:43:00:a1:f5:a0:50:39:26:eb:50:28:62:77:31:21:
52:9d:75:a5:ec:04:0e:da:8a:11:8b:71:07:cc:11:63:c7:e0:
3c:57:95:f1:e2:11:8a:2e:6e:af:c4:8d:65:e9:82:00:05:81:
12:93:21:bc6.3. Sign Certificate Signing Request
-
Generate a self signed root certificate
openssl req \ -x509 \ -nodes \ -newkey rsa:2048 -keyout ca.key \ -subj "/C=CN/ST=Shanghai/L=Shanghai/O=Global Security/OU=IT Department/CN=example.com" \ -out ca.crt -
Generate a certificate signing request
openssl req -nodes \ -newkey rsa:2048 -keyout localhost.key \ -subj "/C=CN/ST=Shanghai/L=Shanghai/O=Global Security/OU=IT Department/CN=localhost" \ -out localhost.csr -
Display the contents of the certificate request
openssl req -in localhost.csr -noout -textCertificate Request: Data: Version: 1 (0x0) Subject: C = CN, ST = Shanghai, L = Shanghai, O = Global Security, OU = IT Department, CN = localhost Subject Public Key Info: Public Key Algorithm: rsaEncryption RSA Public-Key: (2048 bit) Modulus: 00:d8:eb:2e:d7:3c:94:92:a2:e7:35:e3:45:78:40: f6:76:73:dc:70:b9:c6:2f:6f:ea:f6:9b:da:d2:58: fd:ed:5f:e4:c6:76:56:25:35:e4:27:7b:6d:58:2b: 06:71:17:ae:a3:8a:8e:bd:f2:f4:bc:24:64:7d:ea: 4f:8a:2b:66:9d:36:e7:6a:23:0e:02:5a:92:b2:1d: a8:95:33:a6:f5:23:a4:9d:2b:c5:50:69:de:fc:f0: c9:4c:f4:6f:5b:cf:6f:20:3e:52:05:02:32:5e:ae: 81:50:69:13:ac:c8:fb:d8:b9:b7:78:24:e7:1f:ea: 52:6b:f6:ca:71:3e:9c:0a:91:e9:97:59:07:e9:1b: af:1b:c5:c4:14:83:c2:c8:e5:80:cf:bc:4e:ac:65: 0f:d7:69:24:eb:3c:2e:51:c9:88:91:4c:33:10:5e: e3:3d:76:42:e1:e1:65:5b:ef:1a:8c:b9:55:92:b4: 6b:d7:a3:86:78:36:b7:58:6b:e5:d5:38:07:fa:52: bb:87:a1:ae:38:ce:0f:a5:44:1f:c6:41:b3:f2:9a: 1c:2e:22:ea:aa:9f:b0:ec:4a:3b:b8:86:49:08:8c: f9:81:7a:cd:1b:77:b2:31:5e:69:e4:51:cc:a1:1f: ca:01:ce:c1:3a:d7:c8:cf:76:21:44:b3:ed:fc:b9: 91:91 Exponent: 65537 (0x10001) Attributes: a0:00 Signature Algorithm: sha256WithRSAEncryption b9:6a:c8:d1:7b:5b:c9:d4:b4:b3:8f:ed:93:4f:16:00:44:f1: 3f:0a:5b:64:d4:71:f2:d7:5b:71:6e:1e:0e:be:3b:8b:a1:f5: 89:45:b0:33:6c:cf:c1:56:36:71:1a:54:78:d1:2e:90:f6:86: f4:99:8e:c6:ee:d7:64:58:37:22:09:5e:5e:cf:09:eb:06:94: 3b:bc:e7:cd:55:98:48:cf:3e:4c:0a:bd:b7:c5:8d:03:0a:08: 1c:35:10:fb:78:e7:16:6e:8d:c5:f3:87:5a:f8:2b:cd:4a:94: ca:0a:e8:a1:ba:59:96:e7:3d:62:78:5a:a9:24:78:a1:36:6a: c1:2b:4f:6b:54:df:34:41:68:49:01:01:e6:ed:61:c1:8e:80: d4:93:68:7e:8a:68:82:24:c0:62:e7:9b:77:b1:b1:6c:e0:40: b8:4b:64:1b:de:47:a5:1e:6a:21:82:fd:c8:27:50:3f:62:5f: c6:12:89:89:4d:85:82:b6:b9:0b:5f:9e:2a:19:94:13:05:d9: bb:cc:db:0b:1d:58:04:bf:99:2b:8f:3e:ba:29:11:68:b0:4d: 58:d7:07:ac:c1:73:6c:80:a4:3c:ca:19:82:6e:fc:5d:44:ce: 4b:c3:12:8d:6a:35:12:c9:b0:a8:64:47:f7:6d:49:04:68:01: ca:b6:6c:11 -
Sign a certificate request using the CA certificate above
openssl x509 \ -req \ -in localhost.csr \ -CA ca.crt \ -CAkey ca.key \ -CAcreateserial \ -days 10000 \ -out localhost.crt -
Display the contents of the certificate
$ openssl x509 -in localhost.crt -subject -issuer -noout subject=C = CN, ST = Shanghai, L = Shanghai, O = Global Security, OU = IT Department, CN = localhost issuer=C = CN, ST = Shanghai, L = Shanghai, O = Global Security, OU = IT Department, CN = example.com
6.4. Verify Certificate Signature
$ openssl req -x509 \
-nodes \
-newkey rsa:2048 -keyout key.pem \
-days 30 \
-out cert.pem \
-subj "/C=CN/ST=Shanghai/L=Shanghai/O=Global Security/OU=IT Department/CN=example.com" \
-addext "subjectAltName=DNS:example.com,DNS:*.example.com"
Generating a RSA private key
.........................................................+++++
..................+++++
writing new private key to 'key.pem'
-----
$ openssl x509 \
-in cert.pem \
-text \
-noout \
-certopt ca_default \
-certopt no_validity \
-certopt no_serial \
-certopt no_subject \
-certopt no_extensions \
-certopt no_signame | \
grep -v 'Signature Algorithm' | \
tr -d '[:space:]:' | \
xxd -r -p > cert-encrypt-sig.bin
$ od -x -A n --endian=big cert-encrypt-sig.bin
af04 bea5 565e d3af 0156 3796 289e 7860
ba23 969f 7c85 b832 03fc ddb7 1b92 811c
3e53 42ed 7405 aa1b af10 b5b9 2fdc c821
1c47 1783 a78c 9765 7964 b064 9e29 e2f2
9f53 ba98 a533 7589 c6a9 ccf3 d56f dbdb
e796 99ba 0b5b 9f55 f6a1 407d 7d09 5117
e5cc 54a2 1748 ef6b c140 1bce c63c 400d
6faa f5e8 ea8e 2e16 163a 47df 7446 90c6
4d41 8365 53c1 5d2e 8834 eb1e 185d 516d
3b17 5b93 1d71 888e 1a0b 17c4 f861 baac
af8b 441d 0105 08ba 9f1a a8ba 62a5 45f6
56d8 9177 7bec 488b 58e0 f4f6 ec90 a2ce
765b 210b b3bd fbc5 38c5 f884 a362 b4d9
44d1 6718 a86b 6659 7fef 5a92 989f bba6
1801 15fd b94a 0c8b c169 944c c68c e4f1
af9b 6c11 bf58 9f8f 765d 0b35 9b81 0c39
$ openssl x509 -in cert.pem -noout -text
...
Signature Algorithm: sha256WithRSAEncryption
af:04:be:a5:56:5e:d3:af:01:56:37:96:28:9e:78:60:ba:23:
96:9f:7c:85:b8:32:03:fc:dd:b7:1b:92:81:1c:3e:53:42:ed:
74:05:aa:1b:af:10:b5:b9:2f:dc:c8:21:1c:47:17:83:a7:8c:
97:65:79:64:b0:64:9e:29:e2:f2:9f:53:ba:98:a5:33:75:89:
c6:a9:cc:f3:d5:6f:db:db:e7:96:99:ba:0b:5b:9f:55:f6:a1:
40:7d:7d:09:51:17:e5:cc:54:a2:17:48:ef:6b:c1:40:1b:ce:
c6:3c:40:0d:6f:aa:f5:e8:ea:8e:2e:16:16:3a:47:df:74:46:
90:c6:4d:41:83:65:53:c1:5d:2e:88:34:eb:1e:18:5d:51:6d:
3b:17:5b:93:1d:71:88:8e:1a:0b:17:c4:f8:61:ba:ac:af:8b:
44:1d:01:05:08:ba:9f:1a:a8:ba:62:a5:45:f6:56:d8:91:77:
7b:ec:48:8b:58:e0:f4:f6:ec:90:a2:ce:76:5b:21:0b:b3:bd:
fb:c5:38:c5:f8:84:a3:62:b4:d9:44:d1:67:18:a8:6b:66:59:
7f:ef:5a:92:98:9f:bb:a6:18:01:15:fd:b9:4a:0c:8b:c1:69:
94:4c:c6:8c:e4:f1:af:9b:6c:11:bf:58:9f:8f:76:5d:0b:35:
9b:81:0c:39
$ openssl pkeyutl -decrypt \
-inkey pkc1-key.pem -pkeyopt rsa_padding_mode:none \
-in cert-sig-decrypted.bin \
-out cert-decrypted.bin
$ openssl asn1parse -inform der -in cert-sig-decrypted.bin
0:d=0 hl=2 l= 49 cons: SEQUENCE
2:d=1 hl=2 l= 13 cons: SEQUENCE
4:d=2 hl=2 l= 9 prim: OBJECT :sha256
15:d=2 hl=2 l= 0 prim: NULL
17:d=1 hl=2 l= 32 prim: OCTET STRING [HEX DUMP]:886B28CF2FF661E2972966C7E5CC175B393F7620C388B25BA027CE92696856DB
$ openssl asn1parse -inform der -in cert-sig-decrypted.bin \
| grep 'HEX DUMP' \
| cut -d ':' -f4 \
| tr '[:upper:]' '[:lower:]'
886b28cf2ff661e2972966c7e5cc175b393f7620c388b25ba027ce92696856db
$ openssl asn1parse -in cert.pem -strparse 4 -noout -out - \
| openssl dgst -sha256 \
| cut -d ' ' -f2
886b28cf2ff661e2972966c7e5cc175b393f7620c388b25ba027ce92696856db6.5. Generate Certificate with subjectAltName
openssl req -x509 \
-nodes \
-newkey rsa:4096 \
-days 3650 \
-keyout local.io.ca.key \
-out local.io.ca.crt \
-subj "/C=CN/ST=Shanghai/L=Shanghai/O=Global Security/OU=IT Department/CN=*.local.io" \
-addext "subjectAltName=DNS:local.io,DNS:*.local.io"
$ openssl x509 -in local.io.ca.crt -noout -text
Certificate:
Data:
Version: 3 (0x2)
. . .
Subject: C = CN, ST = Shanghai, L = Shanghai, O = Global Security, OU = IT Department, CN = *.local.io
X509v3 extensions:
X509v3 Subject Key Identifier:
35:67:D0:64:8B:2D:F6:62:78:65:CA:6D:A5:6C:FB:4B:67:7F:61:80
X509v3 Authority Key Identifier:
keyid:35:67:D0:64:8B:2D:F6:62:78:65:CA:6D:A5:6C:FB:4B:67:7F:61:80
X509v3 Basic Constraints: critical
CA:TRUE
X509v3 Subject Alternative Name:
DNS:local.io, DNS:*.local.io
. . .6.6. Create CSR with Config File
-
Generate a
server.keywith 2048bitopenssl genrsa -out server.key 2048 -
Create a config file (e.g. csr.conf) for generating a CSR
# csr.conf [ req ] default_bits = 2048 prompt = no default_md = sha256 req_extensions = req_ext distinguished_name = dn [ dn ] # C = <country> C = CN # ST = <state> ST = Shanghai # L = <city> L = Shanghai # O = <organization> # 1.O = <organization> # 2.O = <organization> O = IT Department # OU = <organization unit> # 1.OU = <organization unit> # 2.OU = <organization unit> OU = Developer # CN = <MASTER_IP> CN = developer [ req_ext ] subjectAltName = @alt_names [ alt_names ] DNS.1 = kubernetes DNS.2 = kubernetes.default DNS.3 = kubernetes.default.svc DNS.4 = kubernetes.default.svc.cluster DNS.5 = kubernetes.default.svc.cluster.local #IP.1 = <MASTER_IP> IP.1 = 127.0.0.1 #IP.2 = <MASTER_CLUSTER_IP> IP.2 = 192.168.91.128 [ v3_ext ] authorityKeyIdentifier=keyid,issuer:always basicConstraints=CA:FALSE keyUsage=keyEncipherment,dataEncipherment extendedKeyUsage=serverAuth,clientAuth subjectAltName=@alt_names -
Generate the certificate signing request based on the config file
openssl req -new -key server.key -out server.csr -config csr.conf -
Generate the server certificate using the ca.key, ca.crt and server.csr
openssl x509 \ -req \ -in server.csr \ -CA ca.crt -CAkey ca.key \ -CAcreateserial \ -days 10000 \ -extensions v3_ext \ -extfile csr.conf \ -out server.crt
6.7. How to Convert a Certificate into the Appropriate Format
If your server/device requires a different certificate format other than Base64 encoded X.509, a third party tool such as OpenSSL can be used to convert the certificates into the appropriate format.
|
The PEM format is the most common format used for certificates. Extensions used for PEM certificates are cer, crt, and pem. They are Base64 encoded ASCII files. The DER format is the binary form of the certificate. DER formatted certificates do not contain the "BEGIN CERTIFICATE/END CERTIFICATE" statements. DER formatted certificates most often use the '.der' extension. |
-
Convert x509 to PEM
openssl x509 -in certificatename.cer -outform PEM -out certificatename.pem -
Convert PEM to DER
openssl x509 -outform der -in certificatename.pem -out certificatename.der -
Convert DER to PEM
openssl x509 -inform der -in certificatename.der -out certificatename.pem -
Convert pfx to PEM
The PKCS#12 or PFX format is a binary format for storing the server certificate, intermediate certificates, and the private key in one encryptable file. PFX files usually have extensions such as .pfx and .p12. PFX files are typically used on Windows machines to import and export certificates and private keys. openssl pkcs12 -in certificatename.pfx -out certificatename.pem -
Convert CER and Private Key to PFX
openssl pkcs12 \ -export \ -in certificatename.cer \ -inkey privateKey.key \ -out certificatename.pfx # -certfile cacert.cer